White Paper: Connectivity and control in a networked device world for mobile and non-mobile environments
Abstract
This is the beginning of a smart, multi-layered, and interconnected network of devices. IoT and M2M concept model with connected devices working in layers to control other devices on a wireless network. Primary devices can become controllers of other devices independent on servers forming their own device network. The layered network of devices includes primary, secondary, tertiary, quaternary, and quinary layers. In use, this can be seen as a smartphone controlling a smart watch or remote sensor in a farm field and acting as a hub of control and localized data storage. Data storage would be held in the network as a central point of access and security.
Distribution of functions and power has pushed out to the world of devices. Devices play important roles as they develop more functionality in a networked world. Some devices are sophisticated enough to control and monitor other devices. With this in mind, structure needs to be defined and roles determined to avoid command confusion and data collisions. Taking the structure of a lotus flower, device control hierarchy and command propagation are shown in a layered model.
Author: R. J. Yurkovic
Version 1.0 – Created 11/01/2000
Version 1.1 – Updated 03/08/2004
Version 1.2 – Updated 7/3/2014
1 Lotus Network Theory: Device Connectivity and Control
To explain multiple layers of control and access between devices, applications, and engines, I am introducing a new concept. The Lotus Network Theory of Connectivity and Control (Lotus Network Theory) shows connectivity between various user-oriented or stand-alone components in a network. This model introduces new layers called secondary, tertiary, quaternary, etc. with devices that can be controlled by primary personal devices. Devices control each other through a layer hierarchy without management of the hub control point.
It also introduces a concept of personal sites that offer a user based Web site offering the user and their devices connectivity and access to the WAN world while offering an added protection of privacy.
1.1 Convergence and Enablement
The importance of a network of devices is required due to several factors:
• New devices are emerging in the market
• Technology for small devices is affordable and small
• Wireless technology places devices on the network
• A convergence of applications around communications is occurring (see diagram below)
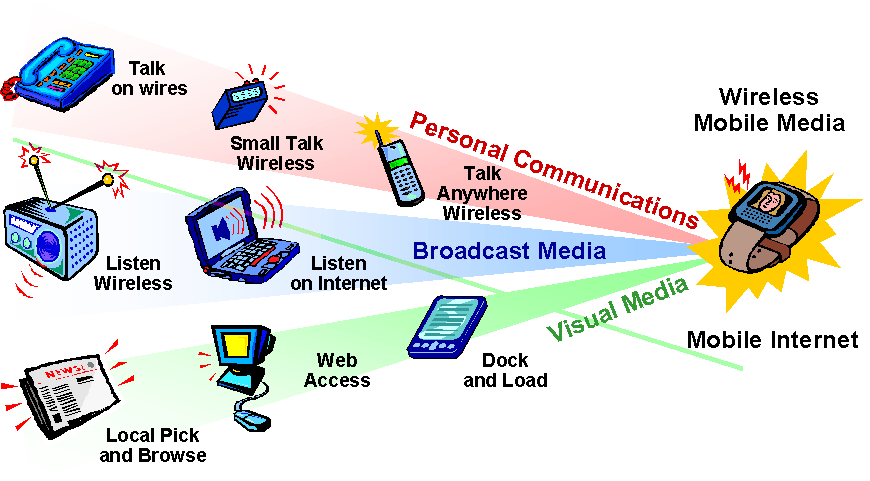
Figure 1 – Technology Convergence
2 The Layered Model
Like a lotus flower’s pedals, the center represents the hub – which is an Internet portal. The next layer is represented by a group of personal sites (personal portals). Together, a selected group of user’s sites form a community net. The next layer is represented by a group of personal (primary) devices such as cell phones, PDAs, and personal appliances. The next layer is represented by a group of secondary devices that are controlled by the primary devices. Additional layers can be added as the device network expands.
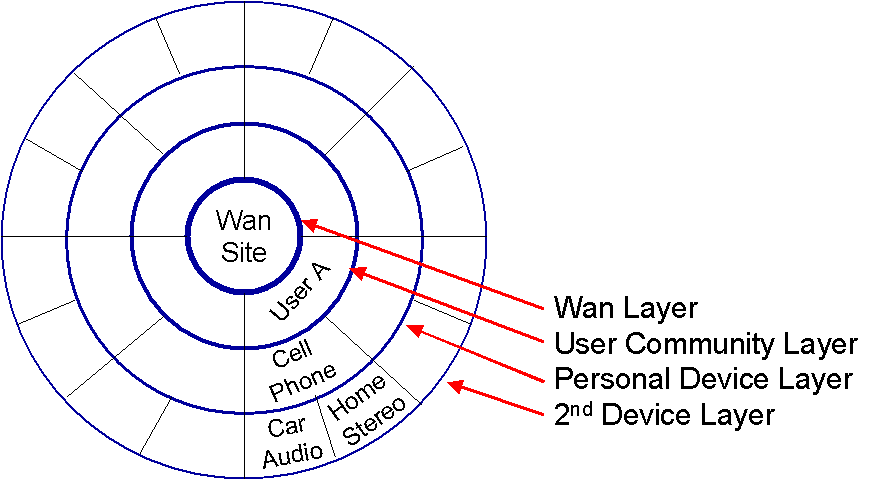
Figure 2 – Lotus Expansion Model
The layers increase as the complexity of devices decreases. Layers for devices could be:
Primary Laptops, tablets
Secondary Mobile phones
Tertiary Smart watches, biometric devices, appliances*
Quaternary RFID sensors, smart cards
Quinary Location sensors, environment sensors
* Appliances could be home, auto, farming, and work equipment.
The hub can be a wireless 802.11x, Bluetooth, RFID, or cellular network.
2.1 Architecture
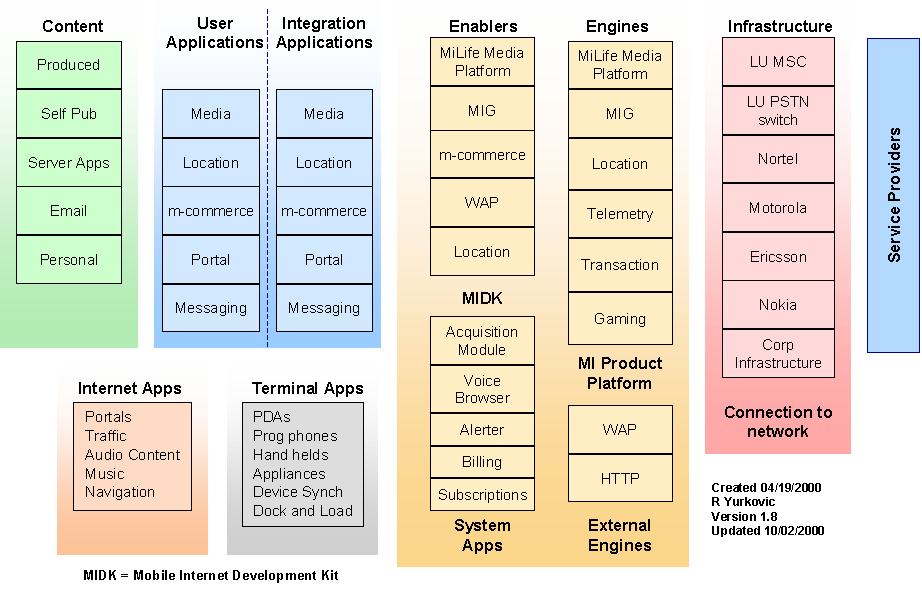
Figure 3 – Wireless Device Application Architecture
There are three engines types in the Mobile Internet platform shown above.
• Engines that interface to systems and infrastructure.
• Engines that support applications
• Engines that transport
2.2 Devices
Devices are self-reliant machines with enough intelligence to monitor and send control signals to other devices. The collection of devices forms an intelligent managed network running programmed applications. Devices are wireless terminals with basic wireless capability or handheld units specializing in data and application processing, tactile input, display output, and media input/output. There are primary and secondary devices.
Primary devices are intelligent devices connected via wireless. They may be handheld/phone units and expanded use cell phones. Examples of primary devices are Compaq IPAQ H3600 equipped with wireless interfaces and cell phones equipped with MP3 players, and Sony’s robotic unit equipped with a Mobile Media Pack. Primary devices can control and program secondary devices.
Secondary devices require connectivity via primary devices using 802.11 or Bluetooth technologies. Examples of secondary devices are TV’s, microwaves, alarm systems, automobile radio units, home entertainment units, and medical monitoring systems.
2.3 Community Net
A group of users can decide to form a community net. This net can share information between themselves easily and still maintain a wall between WANs. Such a net could represent a family, group of friends, corporate business group, or individuals with shared interests. The user server is a personal portal.
2.4 Personal Net
A personal net of devices is comprised of all the devices an individual possesses. Common devices are cell phone, PDAs, Laptop PCs, and specialized networked appliances.
Personal devices can adapt to the user’s needs and can maintain multiple terminal personalities. Personalities modify the user interface and control applications to accommodate the user at a particular point in time and space. For example, the user’s personality A may be set for an office environment controlling and accessing office applications and office appliances (secondary devices: whiteboards, projectors, etc.). Personality B may be set for a home environment controlling and accessing home applications and home appliances (secondary devices: microwaves, televisions, etc.).
2.5 Device Net
A device net is a layer of secondary devices that can be controlled by human interfaces or primary devices. For example, a television with remote control could be a secondary device. A person can control the functions of the television with their hands or with a primary device, such as a PDA that acts like a remote control.
The personal portal is the primary barrier of protection of ensuring personal privacy. The personal site is basically a personal web. All personal information and preferences are held in the portal – instead of at the WAN sites. Personal information resides with the person. The person decides what information to share.
This portal can also act as a base for personal transactions micro billing. The portal can act as a personal bank issuing transactions to various WAN based services. Aggregation of all transactions occurs at the personal portal.
3 Uses
In a use scenario, a farm could deploy devices to monitor conditions such as moisture, heat and chemical composition. If several sensors detect low moisture outside of normal parameters, the devices could signal another device that controls water sprinklers to provide water as needed.
3.1 Application to Mobile Media Platform (MMP)
The MMP enables secondary devices to connect to Primary devices such as mobile phones and connected robotics. Secondary devices can be sensors and control points that relay data back to the primary devices.
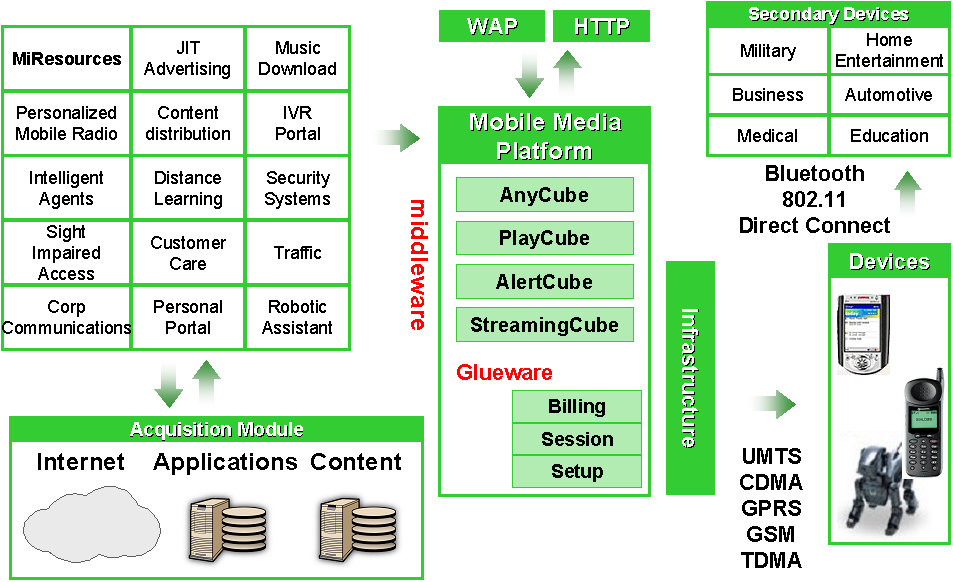
Figure 4 – MMP Architecture and Applications
3.2 Health Services
An example of device to device use is in the health industry and how biometric devices sense and transmit data to a smartphone or central data gateway so that health data can be aggregated and analyzed for values out of expected parameters. Early detection provides a quicker response time in treating a condition for better outcomes. Centralized monitoring facilities have shown to provide better care and response times aiding physicians and care givers in delivering care.
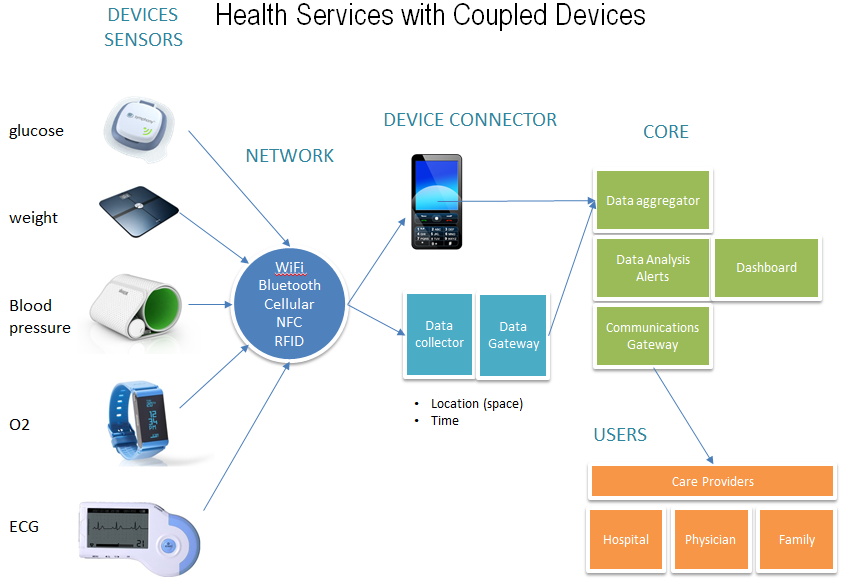
Figure 5 – Health Biometric Devices and Application Architecture